The accelerating convergence of Information Technology (IT) and Operational Technology (OT) systems in manufacturing, a hallmark of Industry 4.0, has significantly expanded the attack surface, rendering traditional security measures ineffective. Cyber incidents impacting these converged environments are increasingly commonplace, prompting a shift in how manufacturing organizations approach cybersecurity.
The expanding risk landscape necessitates a Zero Trust security paradigm. The “Never trust, always verify” principle is no longer theoretical, but an operational imperative, particularly for the vulnerable OT systems that underpin manufacturing processes
Adopting a Zero Trust model in OT is not merely an aftermarket controls upgrade; it represents a strategic pivot essential for maintaining business continuity and resilience in an era of advanced, often AI-powered, cyber threats. OT security models, which historically relied on perimeter defenses, are failing to protect against attackers who can bypass these perimeters or originate from within the organization.
BlastWave is a Zero Trust solution designed for the challenges of manufacturing environments. It provides a triad of protective capabilities: network cloaking, passwordless secure remote access (SRA), and software defined microsegmentation that collectively block entire classes of cyber risk. For Chief Information Security Officers (CISOs) and Chief Information Officers (CIOs), BlastShield delivers tangible benefits: Zero Trust security enhancements designed to maintain uptime and safety, with significantly lower deployment times and operational costs. BlastWave provides a cost-effective and pragmatic way for manufacturers to align with IEC standards.
BlastWave’s solutions:
By implementing BlastWave’s robust Zero Trust model, manufacturing organizations can transform their cybersecurity posture from a reactive cost center into a proactive enabler of operational excellence and a source of competitive advantage.
Industry 4.0, characterized by the adoption of Connected Workers, Lights-Out Factories, and Remote Operations/Augmented Workforce tools (AR/VR), is undergoing rapid transformation, bringing efficiency and operational benefits, but also an expanded attack surface.
Industry 4.0 is characterized by the deep integration of Operational Technology (OT) systems, such as Programmable Logic Controllers (PLCs), Supervisory Control and Data Acquisition (SCADA) systems, and Manufacturing Execution Systems (MES), into enterprise-level systems and data lakes. While beneficial for productivity, this convergence renders the traditional “air gap” that once isolated OT environments, ineffective.
Approximately 50% of OT systems currently connect directly to corporate IT networks, with this number expected to rise to 70% within the next few years. Increased connectivity means that IT vulnerabilities and attacks can spread more readily into OT networks. In the past year, 75% of cyber incidents affecting manufacturing firms occurred in operations with converged IT-OT networks. This increased IT-OT connectivity makes seemingly less critical systems, like an HVAC contractor’s remote access point, a gateway for attackers to reach and compromise operationally critical manufacturing systems. Perimeter defenses alone cannot mitigate threats associated with Industry 4.0.
Stopping These Attacks:
Prevent Hackers from discovering your network and having no credentials to be stolen
Manufacturing OT environments are targeted by a diverse range of threat vectors, each capable of causing significant disruption:
Ransomware has become the most frequent and damaging type of cyberattack against the manufacturing sector. As many as 65% of manufacturing companies have faced a ransomware attack, with the manufacturing industry being the primary target for such extortion attempts. The financial impact is staggering, with average ransom payments substantial and downtime costs accumulating rapidly, sometimes at a rate of millions of dollars per day.
Supply Chain Attacks: Attackers increasingly target manufacturers through their less secure suppliers or third-party vendors. A compromised supplier can inadvertently introduce malware or provide an entry point into the manufacturer’s network. As many as 40% of cyberattacks are estimated to occur via the supply chain. The widely publicized Colonial Pipeline attack, which disrupted fuel supplies in the US, was initiated through a compromised VPN account belonging to a third party, illustrating the potential cascading effects of supply chain vulnerabilities.
Insider Risks: Human factors, whether malicious intent or negligence, remain a significant vulnerability. Employees or contractors with legitimate access can inadvertently or deliberately cause harm. The 2021 Oldsmar water treatment plant incident, where an attacker attempted to poison the water supply, is believed to have involved the exploitation of legitimate remote access credentials, potentially by an insider or someone who had acquired insider credentials.
Legacy System Exploits: Many manufacturing facilities rely on legacy OT systems and components that were designed and deployed decades ago, long before cybersecurity became a significant concern. These systems often run outdated software, lack modern security features, and may no longer receive security patches from vendors, making them vulnerable to exploitation. The persistence of these unpatchable vulnerabilities creates a critical challenge, necessitating security solutions that can protect these systems externally through network cloaking and segmentation, as traditional endpoint security is often not feasible.
Other Pervasive Threats: Beyond these, manufacturers also face threats from sophisticated phishing campaigns (often enhanced by AI), direct attacks on Internet of Things (IoT) and Operational Technology (OT) devices, Distributed Denial-of-Service (DDoS) attacks, cloud security breaches, and the exploitation of zero-day vulnerabilities. Spear phishing and exploiting public-facing applications create infection vectors in many manufacturing breaches.
The financial motivation behind most of these attacks (96% of attacks targeting the manufacturing sector driven by monetary gain) indicates that adversaries are increasingly sophisticated in identifying and exploiting OT systems that can cause maximum operational disruption. This capability increases the pressure on victims to pay ransoms or allows for effective industrial espionage, making proactive and robust defense mechanisms more critical than ever.
Beyond physical damage, breaches can result in an inability to fulfill customer orders, significant loss of brand value, and lasting reputational harm. The operational paralysis from a major OT incident can take weeks or even months to fully resolve, impacting supply chains, customer relationships, and market confidence.
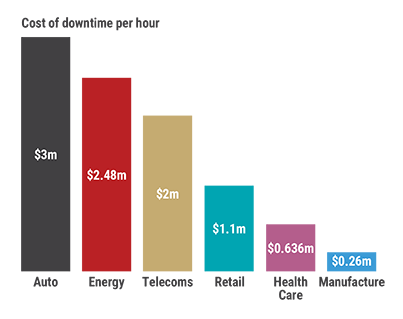
The consequences of a successful cyberattack on a manufacturing OT environment extend far beyond immediate financial losses. While the direct costs of downtime can be enormous, ranging from $200,000 to $2 million per incident for resilience or availability issues, and averaging $1.9 million per day of downtime in ransomware cases, the indirect and long-term impacts can be even more devastating.
Cyberattacks can cause permanent damage to expensive plant machinery and equipment, as seen in the 2014 attack on a German Steel Mill. In this incident, attackers used spear-phishing emails to steal credentials, gained access to the office network, and then pivoted to the production systems. They compromised PLCs controlling a blast furnace, preventing its proper shutdown and causing “massive” physical damage, with repair costs estimated in the millions of dollars.