

BlastShield is a zero-trust network access solution that helps organizations implement a zero-trust architecture.
Instead of relying on enhanced identity governance (EIG), complex layers of micro-segmentation, or cloud-based gateways, BlastShield utilizes a software-defined perimeter (SDP) approach for more granular access controls and reduced risk from stolen credentials and complex management.
Start a free trialThe BlastShield Security Gateway is a hardware-independent software package that can be installed in a VM or container, or purchased as a pre-installed appliance from our partners (see the bottom section of the page for appliances). It delivers Network Cloaking, terminates Secure Remote Access connections, and uses software-defined segmentation to secure OT networks.


Our Zero Trust client for OT networks is designed to integrate seamlessly into your existing operations without disrupting them. No more clunky interfaces, web browser limitations, or frustrating roadblocks. Our client empowers your team to work the way they always have, with the added confidence that a robust Zero Trust framework shields your critical infrastructure. Windows, Mac, and Linux are supported.
Our passwordless authenticator puts the power of biometrics and your mobile device directly into your hands. It's security that's as natural as unlocking your phone. We understand the frustration of constantly changing passwords and the vulnerability of those easily stolen credentials. Authentication is performed by combining a QR code challenge-response with localized biometric authentication and the device keystore to prevent credential theft and AI-powered attacks, requiring a human-in-the-loop. IOS and Android are supported.

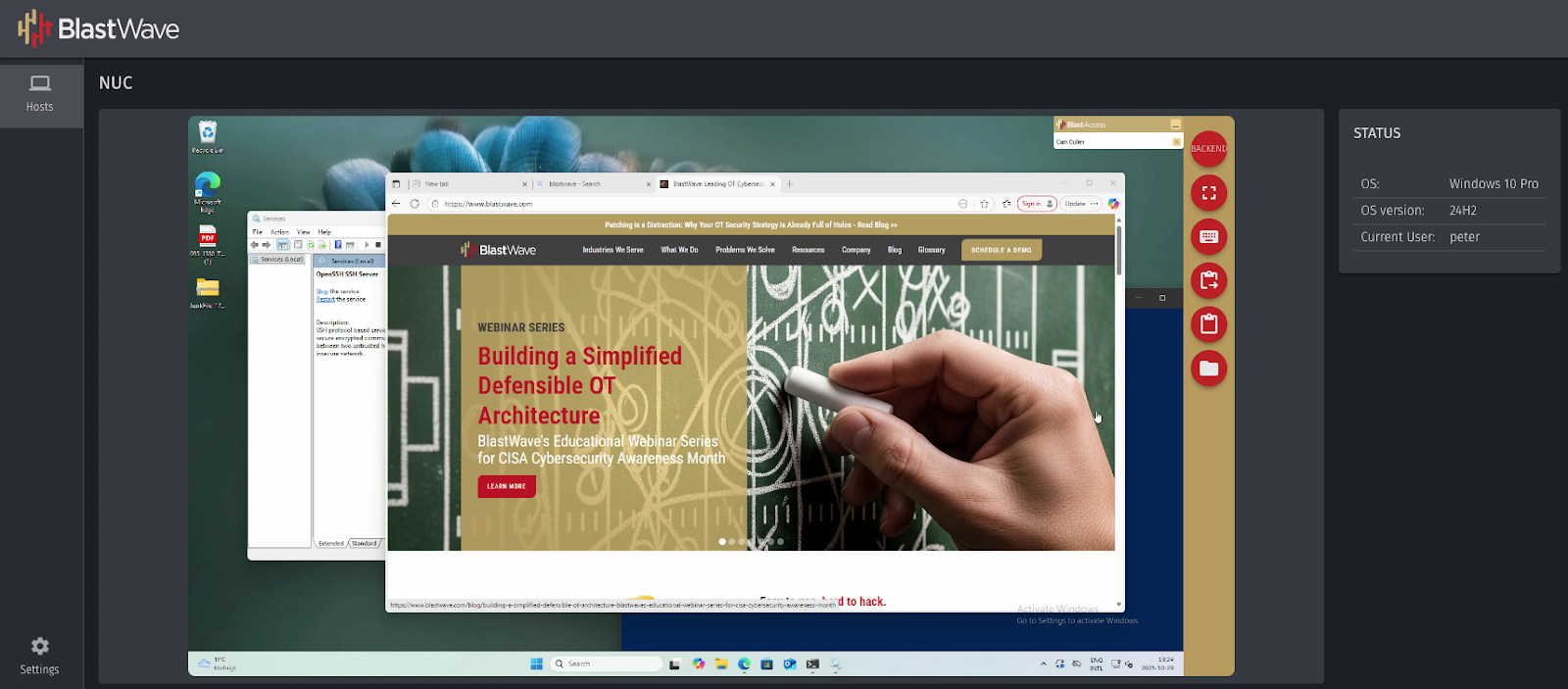
If your business requires tightly managed remote desktop connectivity with session recording for remote access, BlastAccess delivers this functionality with high performance. Leveraging the same phishing-resistant authentication protection as the BlastShield client, BlastAccess eliminates the weaknesses of PAM and web-based RDP solutions by removing open ports and preventing browser hijacking and password theft. Session recording streams desktop activity to a storage system, providing security, forensics, and audit logging for all remote maintenance activities.
Our lightweight agent instantly transforms any server into a Zero Trust stronghold. It's like wrapping each critical asset in an impenetrable shield. They simply can't connect without a verified BlastShield client. No exceptions. No backdoors. Windows, Mac, and Linux are supported.


Our Orchestrator is the conductor of your Zero Trust orchestra, ensuring seamless, real-time policy enforcement across your entire network. No more static, cumbersome rule sets. Our Orchestrator dynamically adapts to your evolving needs, connecting everything with the right policies in real-time. The Orchestrator can be deployed on-premises or in the cloud, depending on the organization's business needs.
.svg)
Every user and device must be authenticated and authorized before access, regardless of location.
Learn MoreUsers are granted only least privilege access, limiting the ability to see and move within the network laterally.
Learn MoreThe network is divided into isolated segments to prevent lateral movement and contain the impact of breaches.
Learn More

Ten years ago in Ukraine, 225,000 people lost power when hackers used stolen credentials to exploit OT networks built on implicit trust. Today, the same flaw persists. BlastWave removes visibility, passwords, and lateral movement, denying attackers all access.
Getting started with BlastShield is easy and free. Follow the three steps below and get up and running fast.
%20(1).svg)
Create a Free Trial
Account
.svg)
Download the BlastShield Authenticator & Client
.svg)
Make Your Host Invisible
In Minutes
Privacy Policy | Cookie Policy | © 2025 BlastWave, Inc. All Rights Reserved
This website uses cookies to ensure you get the best experience. More Info