When Luck Is More Useful Than Your Firewall: The Oldsmar Hackopedia Incident
Welcome back to the Hackopedia Anniversary Series. In this blog series, I am dissecting some of the most (in)famous OT hacks to understand the mechanics of failure and the urgent need for defense. We started with the Ukraine power hack, and today I am looking back on a near-miss that should have been a wake-up call for every municipal leader in America: the 2021 Oldsmar Water Treatment Plant incident.
When the industry talks about Critical Infrastructure, people usually imagine the sprawling complexity of the power grid or the data centers of major banks. But the Oldsmar incident reminded us that the most dangerous vulnerabilities often sit in the quiet, underfunded corners of our water utilities, where the barrier between safe drinking water and mass poisoning can be as thin as a single shared password.
The Super Bowl Weekend Nightmare
Let’s set the scene. It was Friday, February 5, 2021. The Tampa Bay area was buzzing with energy as it prepared to host Super Bowl LV. Just 15 miles away from the stadium, in the small city of Oldsmar, a plant operator sat quietly monitoring the city's water treatment consoles.
At 8:00 AM, he noticed the mouse cursor on his screen move. He assumed it was a supervisor checking in via TeamViewer, and didn't think much of it.
Five hours later, the cursor moved again. But this time, it wasn't a check-in. The operator watched, frozen in disbelief, as the invisible hand clicked through the system menus, navigated to the Sodium Hydroxide (Lye) controls, and changed the setting from 100 parts per million to 11,100 parts per million.
In seconds, the attacker had commanded the system to pump a lethal dose of caustic chemical into the water supply of 15,000 people.
The Terrifying Factor: Luck
The only reason you aren't reading about a mass casualty event in Florida today is luck.
There was no sophisticated AI-driven threat detection that stopped the attack. There was no "Zero Trust" architecture blocking the lateral movement. The firewall didn’t catch it.
The attack was thwarted because a human being happened to be looking at the right monitor, at the right second, and had the presence of mind to grab the mouse and reverse the changes immediately.
If that operator had been in the bathroom, getting a coffee, or distracted by a phone call, it would have taken 24 to 36 hours for the poisoned water to hit the main system. While pH sensors might have detected it later, they might not have.
If this had been a more sophisticated attacker (e.g., Volt Typhoon), they would have altered not only the mixture but also the sensors, and the outcome would have been different; luck may not have held out.
Water and Power: The Soft Underbelly
The Oldsmar hack highlighted a terrifying reality of the OT (Operational Technology) sector, particularly in water systems.
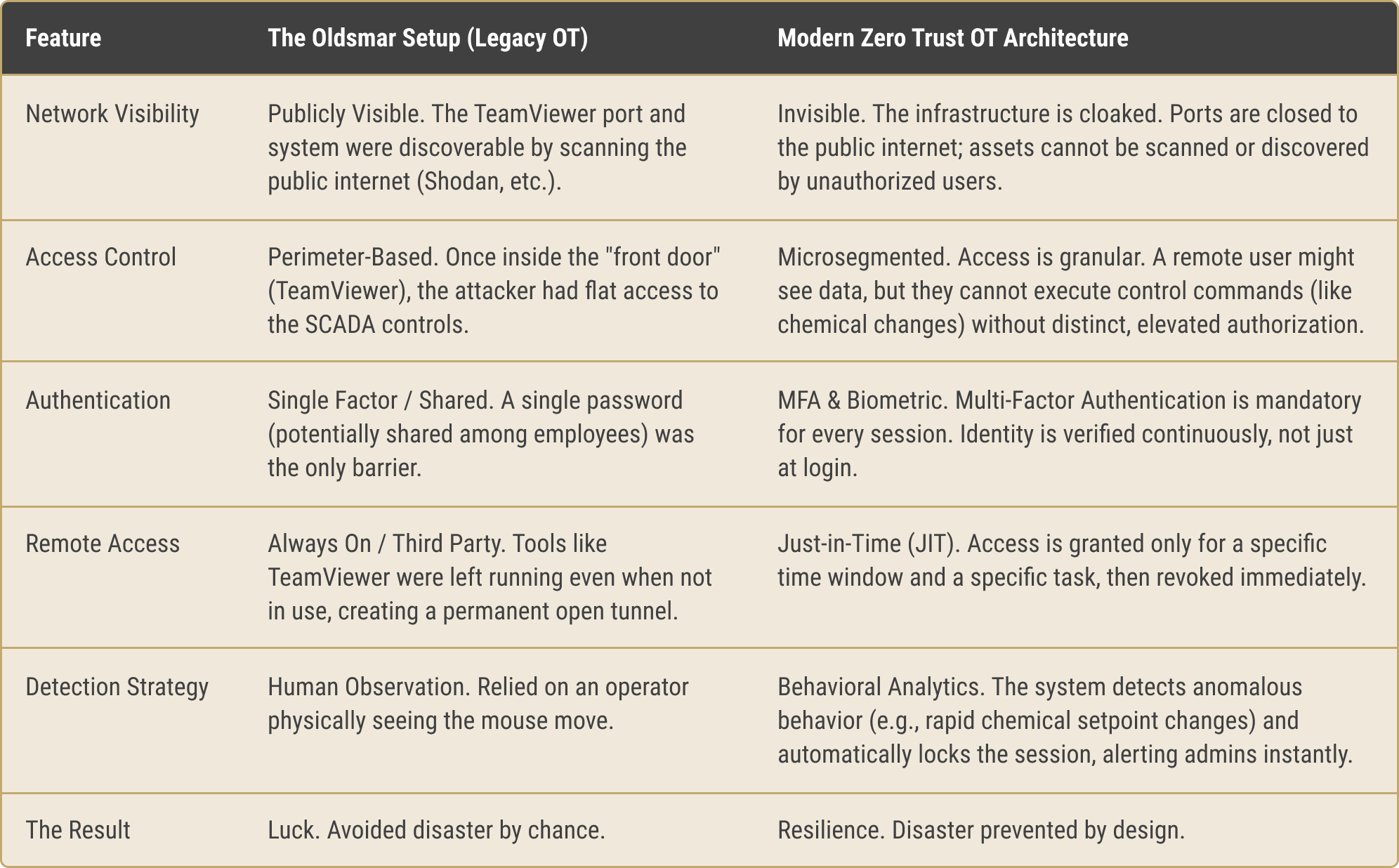
- Legacy Dependencies: The facility was reportedly using an outdated version of Windows (Windows 7) and relied on TeamViewer for remote access. This is standard operating procedure for thousands of water utilities across the country that lack the budget for high-end cybersecurity teams.
- The "Air Gap" Myth: Many utilities believe they are "air-gapped" (disconnected from the internet). Oldsmar proved that if you have a vendor login or a remote access tool, your air gap is a myth. You are online and vulnerable.
- Kinetic Consequences: Unlike a data breach where credit card numbers are stolen, a breach in Water can have kinetic consequences. Equipment breaks, pumps stop (or go into turbo mode), or water becomes toxic. The stakes aren't financial; they are physical, and ultimately, humans are at risk.
Why We Can't "Patch" Our Way Out of This
The industry response to Oldsmar was a flurry of advisories: "Change your passwords," "Update TeamViewer," "Patch Windows."
While necessary, these are band-aids on a bullet wound. The problem isn't just poor password hygiene; it's the architecture of connectivity itself. In an era where critical infrastructure is constantly probed by nation-states and script kiddies alike, visibility should be a privilege, not a default.
I look at Oldsmar and see the desperate need for software-defined perimeters and OT-specific masking. If the attackers couldn't see the TeamViewer port, they couldn't have exploited it. If the network was segmented so that remote access didn't grant god-mode administrative rights over chemical controls, the cursor would have never moved. What would the difference be if Oldsmar used the latest OT protection solutions?
The Takeaway
The Oldsmar hack remains one of my favorite case studies for Hackopedia because it had a happy ending, but it scares me more than almost any other. It proved that for many of our vital services, our primary line of defense isn't technology, it's the hope that someone is watching the screen when the mouse starts moving.
We have to stop relying on luck. We have to make our critical infrastructure invisible to attackers, because next time the operator might be on a coffee break. I don’t want to write any new Hackopedia entries on water utilities this year if I can help it. Unlike many OT water cybersecurity solutions, BlastWave is extremely cost-effective for water (we have customers deployed for less than $10,000), and we see it as our duty to help protect these systems, which are often overlooked by IT- and enterprise-centric solutions.
A hacker nearly poisoned Oldsmar’s water using visible remote access—not malware. BlastWave reveals why invisibility, not detection, is the future of OT security.
Explore the complete analysis of 23 OT attacks that defeated firewalls, VPNs, and air gaps.










.svg)